How real are threats to our financial and personal information?
According to UTMB’s Information Security Director, Bob Shaffer, they are very real.
"Just watch the nightly news," said Shaffer. "It seems that a month doesn’t go by without hearing about a data breach, affecting millions of people. In fact, according to an annual report published by Verizon and the U.S. Secret Service, 97 percent of these breaches can be avoided by applying basic to intermediate security controls."
Over the years, Shaffer and his team have been monitoring the effectiveness of installed information security controls at UTMB. Of the 20 or so institutional controls deployed, the most effective one implemented so far is user awareness and education.
Shaffer said that his team noticed a sharp spike in reported security incidents after they initiated a comprehensive education and awareness program in 2010, which included lectures at new employee orientation, Impact newsletter articles, incident notification alerts on the iUTMB home page, blogs on the Information Security website and informal talks with various departments. Following the spike, a steady but consistent decline in reported incidents has been noted. Shaffer attributed the success of UTMB's information security program to an educated workforce and talented technical personnel.
However, he added that while user education and awareness is key to any effective security program, it’s only a part of the puzzle.
"All it takes is one person with the right data access level to share his or her username and password with someone who’s not supposed to have it and the best laid information security program is relatively useless," said Shaffer.
In July, UTMB experienced a phishing attack (email scam with the intent of stealing usernames and passwords) that targeted more than 11,000 UTMB employees -- close to UTMB's entire workforce. Fortunately, Shaffer said there were incident response plans and security controls in place to mitigate the institutional impact associated with these types of attacks.
"Phishing emails are quickly brought to our attention shortly after the initial ones are received by the user community," said Shaffer. "Internet firewall controls were immediately put in place, preventing future emails with the same content from reaching its intended recipients and preventing access to malicious websites that were linked in the message. Because these emails look authentic and appear to be coming from UTMB departments, such as the IS helpdesk or HR, they can easily be interpreted as legitimate requests, tricking people to unknowingly give up their username and passwords. In this particular case, the described incident response process and implemented security controls were 99.78% effective in protecting us from this threat. However, an estimated 27 people gave up their username and associated password."
Shaffer added that over the course of the last year, there has been a steady increase in the number of phishing attacks. The effort that’s been applied to the formatting, communication style and branding of these emails and Web pages are becoming more sophisticated, making it very difficult for users to identify it as a scam at first glance. These scams are beginning to pose a significant threat to the confidentiality, integrity and availability of personally identifiable and protected health information. Throughout the world, phishing activity has been attributed to individual account compromises that have resulted in stolen paychecks, breaches of confidential data, identity theft and reputational harm to people and institutions.
"A 99.78% effective rate of protecting us from these attacks is not good enough," said Shaffer. "Additional protections need to be put in place to further reduce the risks."
Starting Sept. 1, employees who remotely access UTMB’s network using VPN or Citrix will require a username, password and a second authentication factor. The process is simple and straight forward, and will either involve an acknowledgement of a message that is sent to your phone (one tap approval), an acknowledge of a phone call to the phone number on file, or by entering a six-digit code that is generated from an application installed on your phone or from a hardware token that has been issued to you.
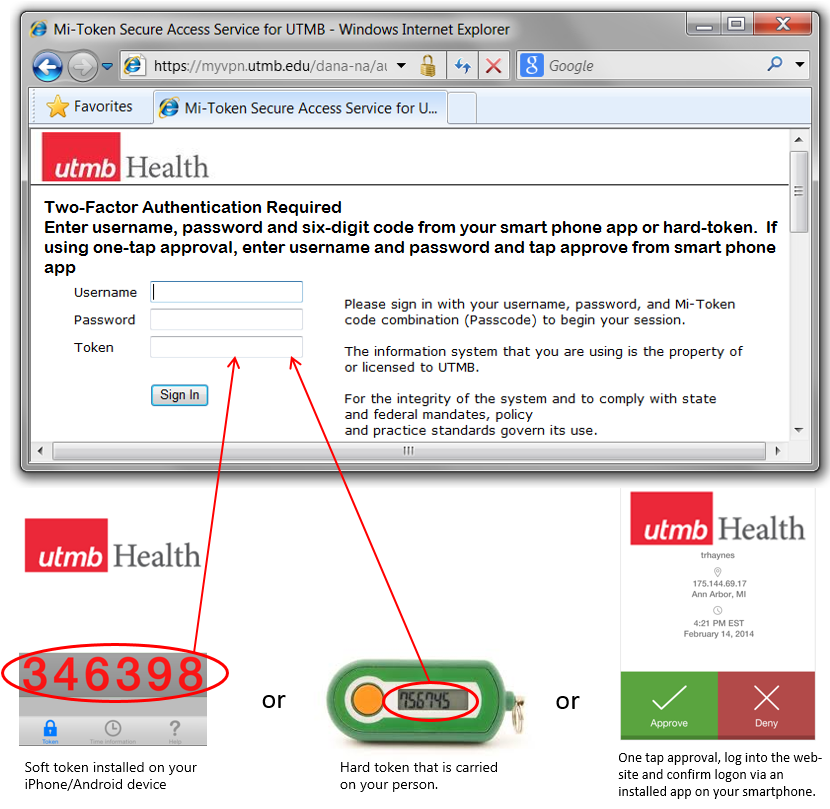
This change will initially impact personnel who have logged on to the UTMB network using the Citrix or VPN gateway within the last 90 days. Identified users will be contacted directly with instructions on how to setup and use the application.
For more information, contact Bob Shaffer at rvshaffe@utmb.edu. If you receive an email that looks like it may be a scam or you are unsure whether to click on it, please forward the email to the Computer Incident Response Team (CIRT) for verification. They can be reached by email at iso@utmb.edu.